Setting up IPsec between UniFi and OPNsense
As safe as possible… ‘Sigh’
So yes, I do understand you want to configure an IPsec tunnel between an UniFi router and OPNsense device. Right under here is what you’re looking for! Now I do expect you already know how IPsec works and what local and remote networks mean. This page is solely meant to help you out to get the tunnel up and running.
PLEASE NOTE!
This guide is based on an older version of both an USG and OPNsense.
I currently do not have access to an USG (or UDM for that fact) and can therefor not update this page as easily.
This guide therefor may or may not work out well for you.
The UniFi controller settings
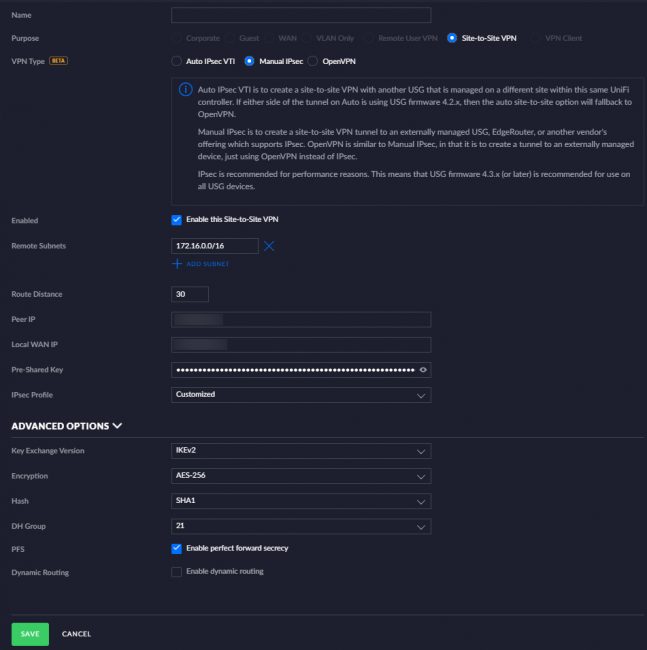
Here are the settings you need on the UniFi side:
Standard options:
- Name: Name it whatever you want!
- Enabled: Yes
- Remote subnets: Put any remote subnet in here that you want the USG to be able to reach to.
- Route Distance: Default is fine, unless needed otherwise.
- Peer IP: The remote IP of the OPNsense you want to terminate your IPsec tunnel to.
- Local WAN IP: The IP of the interface you want to terminate the tunnel on.
- Pre-Shared Key: Make this something vague and long and don’t share it. Read below for best practices.
Advanced options:
- Key Exchange Version: IKEv2, it’s just better. If a device supports it. It supports better encryption, lower bandwidth use, resists network changes (MOBIKE), more reliability and it’s more resistant to DoS attacks.
- Encryption: AES-256, AES-NI is almost default by now… If you don’t have this forget it. AES-128 is fine enough though, 256 gives you around 40-50% more overhead. But it’s harder to crack.
- Hash: SHA1. Yes, I wish SHA256 was an option within the controller. Because it is in the CLI…
- DH Group: 21 at least in combination with AES-256. 20 is fine with AES-128.
- PFS: Gives the assurance that future session keys will not be compromised in case older long-term ones are.
- Dynamic Routing: Disable this, it’ll otherwise just not work.
Save it!
OPNsense settings
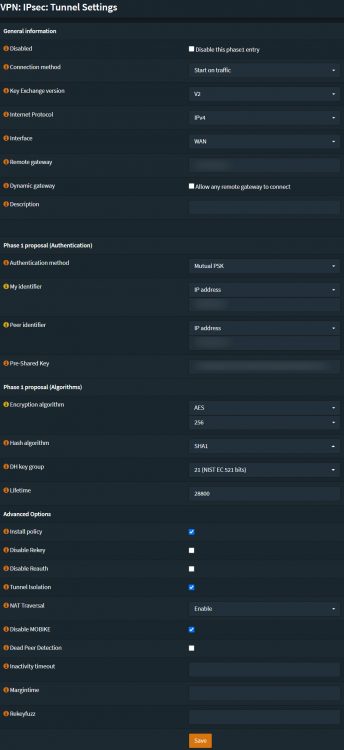
Here are minimal settings you need on the OPNsense side:
Phase 1:
- Connection method: Use whatever, I use start on traffic for my case.
- Key Exchange Version: V2. Like it says above, it’s just better. If a device supports it. It supports better encryption, lower bandwidth use, resists network changes (MOBIKE), more reliability and it’s more resistant to DoS attacks.
- Internet Protocol: IPv4
- Interface: Pick what the IPsec tunnel should terminate on.
- Remote gateway: The IP of the UniFi gateway you want the tunnel to terminate onto.
- Authentication method: Mutual PSK
- My identifier: Use IP address. The same IP used in ‘Peer IP’ in the UniFi GUI.
- Peer identifier: Use IP address. Use the same IP that is used on ‘Local Wan IP’ in the UniFi GUI.
- Encryption algorithm: AES-256
- Hash algorithmb: SHA1
- DH key group: 21
- Lifetime: 28800, this time is used underwater in UniFi.
- Install policy: Enabled
- Tunnel Isolation: Enabled or disabled, try what works for you. It worked better for me.
- Disable MOBIKE: Your specific usecase.
Save it!
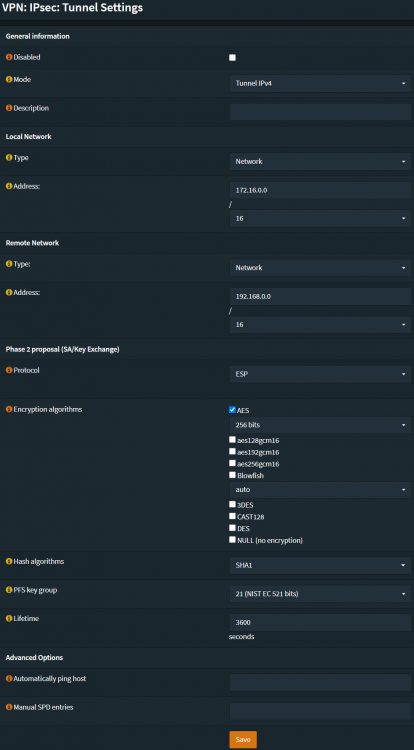
Phase 2:
- Mode: Tunnel IPv4
- Local network: Use any type and setting you require.
- Remote network: Use any type and setting you require.
- Protocol: ESP. Always use ESP.
- Encryption algorithms: AES-256
- Hash algorithm: SHA1
- PFS key group: 21
- Lifetime: 3600. This is the default time UniFi uses.
Save it!
Your tunnel should now work. If not, be sure to contact me!